Information






Big Data | Case Studies | Cyber Security | Data Centres | Information | Security | Top Carousel | July 21, 2016
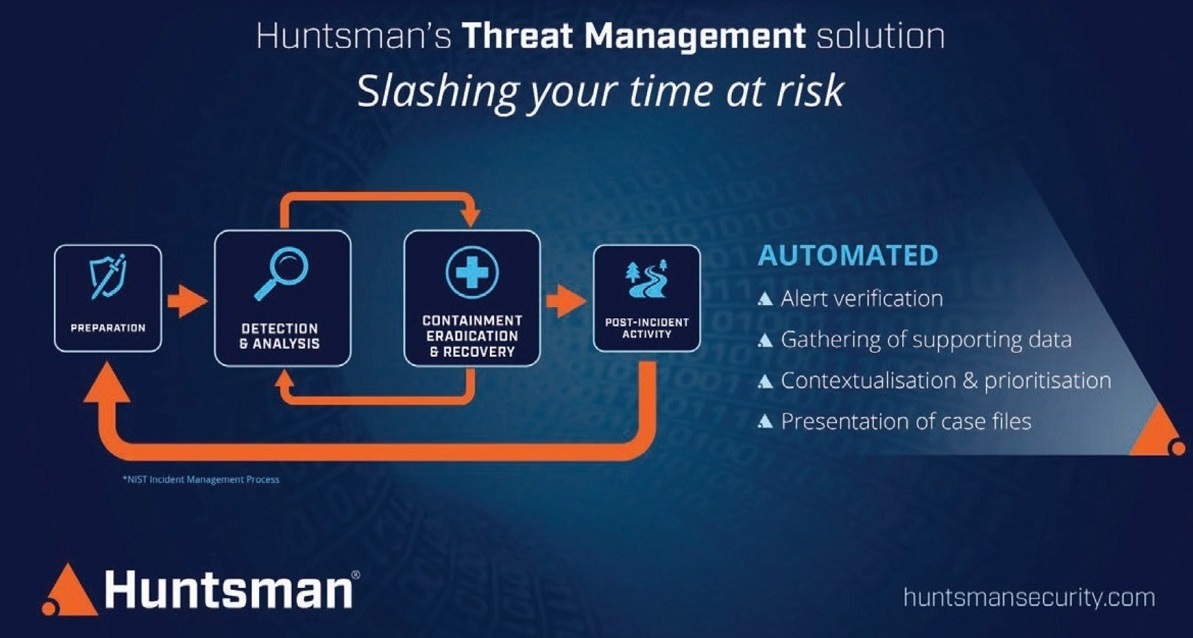
Locating a new weapon for Australia’s data detectives











Communication | Cyber Security | Data Centres | Information | Movers & Shakers | Security | July 11, 2016


