Intel Security has released its latest McAfee Labs Threats Report: August 2015 which includes a five-year retrospective marking the anniversary of Intel’s announcement that it would buy McAfee. To celebrate this the report includes discussion from Intel and McAfee thought leaders on which of their 2010 predictions have materialised – with the following highlights:
- Intel Security foresaw threats targeting hardware and firmware components and threatening runtime integrity
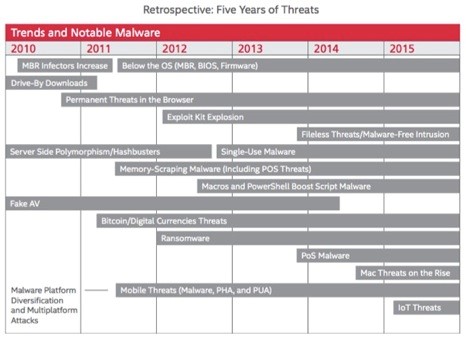
- Increasingly evasive malware and long-running attacks did not surprise McAfee Labs but some of the specific tactics and techniques were unimagined five years ago
- Although the volume of mobile devices has increased even faster than expected, serious broad-based attacks on those devices has grown much more slowly than McAfee Labs thought
- New attacks and breaches against IoT devices are just the beginning
- Cloud adoption has changed the nature of some attacks, as devices are attacked not for the small amount of data that they store, but as a path to where the important data resides
- Cybercrime has grown into a full-fledged industry with suppliers, markets, service providers, financing, trading systems, and a proliferation of business models
- Businesses and consumers still do not pay sufficient attention to updates, patches, password security, security alerts, default configurations, and other easy but critical ways to secure cyber and physical assets
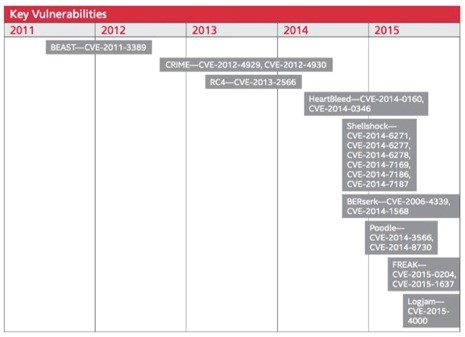
- The discovery and exploitation of core Internet vulnerabilities has demonstrated how some foundational technologies are underfunded and understaffed
- There is growing, positive collaboration between the security industry, academia, law enforcement, and governments to take down cybercriminal operations
Mike Sentonas, Vice President, Chief Technology Officer, Security Connected, Intel Security (quoted below) is available for local comment.
Threats & Key Vulnerabilities 2010-2015:
GPU attacks
One specific focus of the latest report is the potential for future advancement of graphics processing units (GPU) attacks.
Whilst malware attacks on graphics processing units (GPUs) have been around for years, GitHub, the world’s largest code host recently brought the topic to the forefront of attention with posts about proof-of-concept projects that together claim to use GPUs as an instrument of evasion by running code, and storing data, on GPUs—where no one is looking.
The scenarios suggest hackers will attempt to leverafe GPUs for their raw processing power, using them to evade traditional malware defenses by running code nd storing data where traditional defenses do not normally watch for malicious code.
The report looks into the topic in more detail and shows what defenses Intel Security offers to protect against this.
Q2 Cyber attack statistics:
In addition, the report presents an update on cyber attacks recognized by Intel Security during Q2 2015:
- Ransomware. Ransomware continues to grow very rapidly – with the number of new ransomware samples rising 58% in Q2. The total number of ransomware samples grew 127% from Q2 2014 to Q2 2015. McAfee Labs attributes the increase to fast-growing new families such as CTB-Locker, CryptoWall, and others
- Mobile slump. The total number of mobile malware samples grew 17% in Q2. But mobile malware infection rates declined about 1% per region this quarter, with the exception of North America, which dropped almost 4%, and Africa, which was unchanged
- Spam botnets. The trend of decreasing botnet-generated spam volume continued through Q2, as the Kelihos botnet remained inactive. Slenfbot again claims the top rank, followed closely by Gamut, with Cutwail rounding out the top three
- Suspect URLs. Every hour in Q2 more than 6.7 million attempts were made to entice McAfee customers into connecting to risky URLs via emails, browser searches, etc
- Infected files. Every hour in Q2 more than 19.2 million infected files were exposed to McAfee customers’ networks
- PUPs up. Every hour in Q2 an additional 7 million potentially unwanted programs (PUPs) attempted installation or launch on McAfee-protected networks