
Written by Guy Matthews, Editor of NetReporter.
Security provisions for data and applications relied for decades on the same sort of architecture. The typical model was based around a hub and spoke structure, and was heavily hardware-centric. It was also supported by private MPLS circuits to connect everything together. We’re talking about a world of centralized applications living inside the corporate perimeter with only modest volumes of outbound Internet traffic and a time when remote working was the exception not the rule.
Mauricio Sanchez, Research Director, Network Security, SASE & SD-WAN with analyst firm the Dell’Oro Group, says this cosy scenario was ripped up in 2020 when COVID struck. Now post pandemic, we’re into a world of hybrid work with employee time split between the office and any number of other possible end points. The security implications are huge, he notes: “The cost of the average corporate data breach is now over $4 million,” he says. “That’s a significant amount, and that’s just the average. Some breaches are at a much higher level.”
Sanchez cites a recent McKinsey Report indicating that 58% of US employees are now hybrid workers, 10 times the figure from before the pandemic: “This is the new normal and here to stay,” he says. “For all these reasons, the legacy network fell flat during the pandemic. In any case, old MPLS circuits are no longer enough once cloud applications become the norm. The amount of traffic piped between points in the network has become much greater, with more money needing to be spent in order to upgrade to faster legacy pipes. The security stack has become a choke point on the perimeter. The hardware-centric view just doesn’t work as well as it did in the past. Plus we now have a poor app experience among users.”
This background, he believes, is what’s been setting the stage for a conversation around Secure Access Service Edge, or SASE: “On the one hand you have SD-WAN, and the promise of being able to reduce the operational costs of the network, and on the other you’ve got a new breed of cloud-delivered security solutions in the form of SASE,” he explains. “We’ve seen these two being combined over the last couple of years to drive a new topology. They’re coming together in service of the hybrid, cloud-centric enterprise.”
Figure 1: Enterprise SASE spend
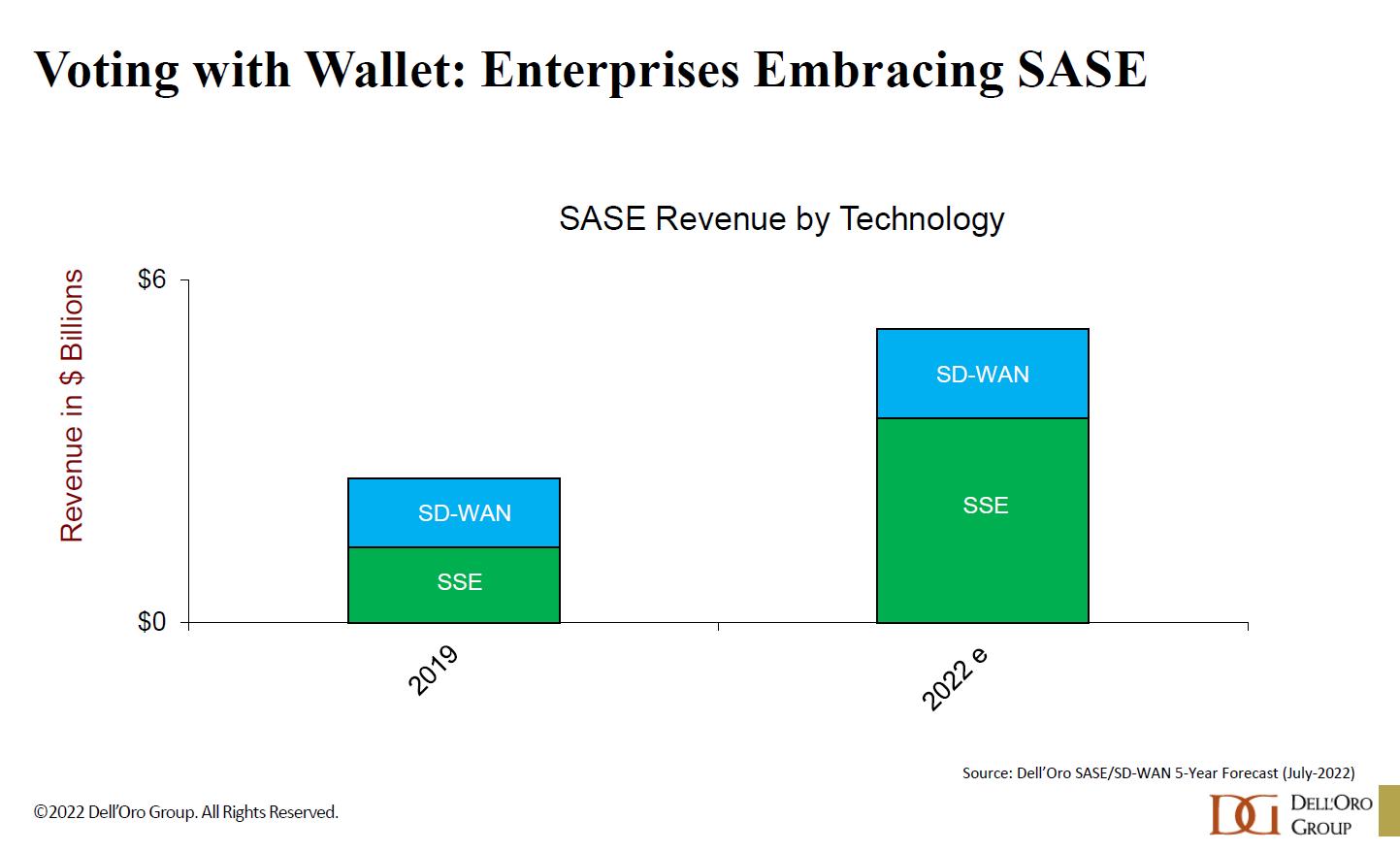
Sanchez says Dell’Oro has measured a sizable increase in the amount that enterprises have been spending on SASE: “We’re on track to hit that $6 billion figure by the end of this year,” he notes.
To find out more about what SD-WAN and SASE really mean for enterprises, Sanchez taps into a panel of expert stakeholders, starting with Craig Connors, VP & GM of VMWare’s SASE Business: “A lot of people forget that the SASE term was actually coined prior to the pandemic,” he points out. “The shifts we’ve talked about were happening already.”
In addition to the obvious SASE driver of remote work, Connors also mentions rising levels of IoT devices, and all the applications that are moving to the edge into various clouds. Then there’s the matter, he says, of rising cyber-attacks in part driven by cryptocurrency and the new ways it offers to monetize illegal activity: “We were already rethinking how to connect and secure these new emerging use cases,” he says. “But it’s hard to pin down exactly what SASE is because so many different vendors claim so many different things. So the priority is to go back to the use cases and look at what you’re trying to accomplish.”
Parag Thakore, Senior Vice President with security platform Netskope, notes that with SD-WAN, as much as with SASE, enterprises want a consistent, uniform performance combined with security, not just to branch offices but to every user device, IoT endpoint or multi-cloud environment. “People are talking about being application aware and context aware,” he says.
Marc Cohn is Leader of the Security Test & Certification Incubation Group with the MEF standards body. He says what MEF is trying to do is recognise SASE as an architecture, catering to the traditional service provider customer base that the organisation serves: “Then we can try to provide a language and a set of standards that can help a service provider manage this multi-vendor environment we face,” he claims. “That’s the role of a SASE standard, and a Zero Trust standard which is the other important companion standard to SASE that we’re addressing in the MEF.”
Central to the SD-WAN and SASE conversation is the choice between dealing with a complicated multi-vendor marketplace for solutions versus opting to outsource to a managed service provider. Thakore says that Netskope always wants, by instinct, to offer customers flexibility and choice: “Successful SASE would imply fewer vendors, simpler operations, reduced complexity, all as part of lower costs,” he argues. “But we understand that it is a journey, not a matter of ‘rip and replace’.”
Options, he says, include the purchase of many individual products that are part of the SASE architecture, requiring tight and deep partnerships and integrations with many security and networking players: “On the other side, some want simplified operations and the need to connect remote users IoT devices, branch offices, multi cloud environments, all in a single fabric,” he says. “In that case, you can purchase an entire converged SASE platform. Both options should be supported. I think flexibility and choice are the key.”
Cohn of MEF believes the longer-term trend is a move away from reliance on just a single vendor: “I think we’re all going to move to multiple vendors and those multiple vendors are going to provide a richer and broader set of cybersecurity functions and applications that are going to be delivered in the SASE environment,” he claims. “But as Parag says, there’s no one size fits all. Let’s acknowledge that there’s a need for vendor provided solutions as well as managed services. That’s why we’re seeing demand along those lines.”
Figure 2: SASE consumption trends
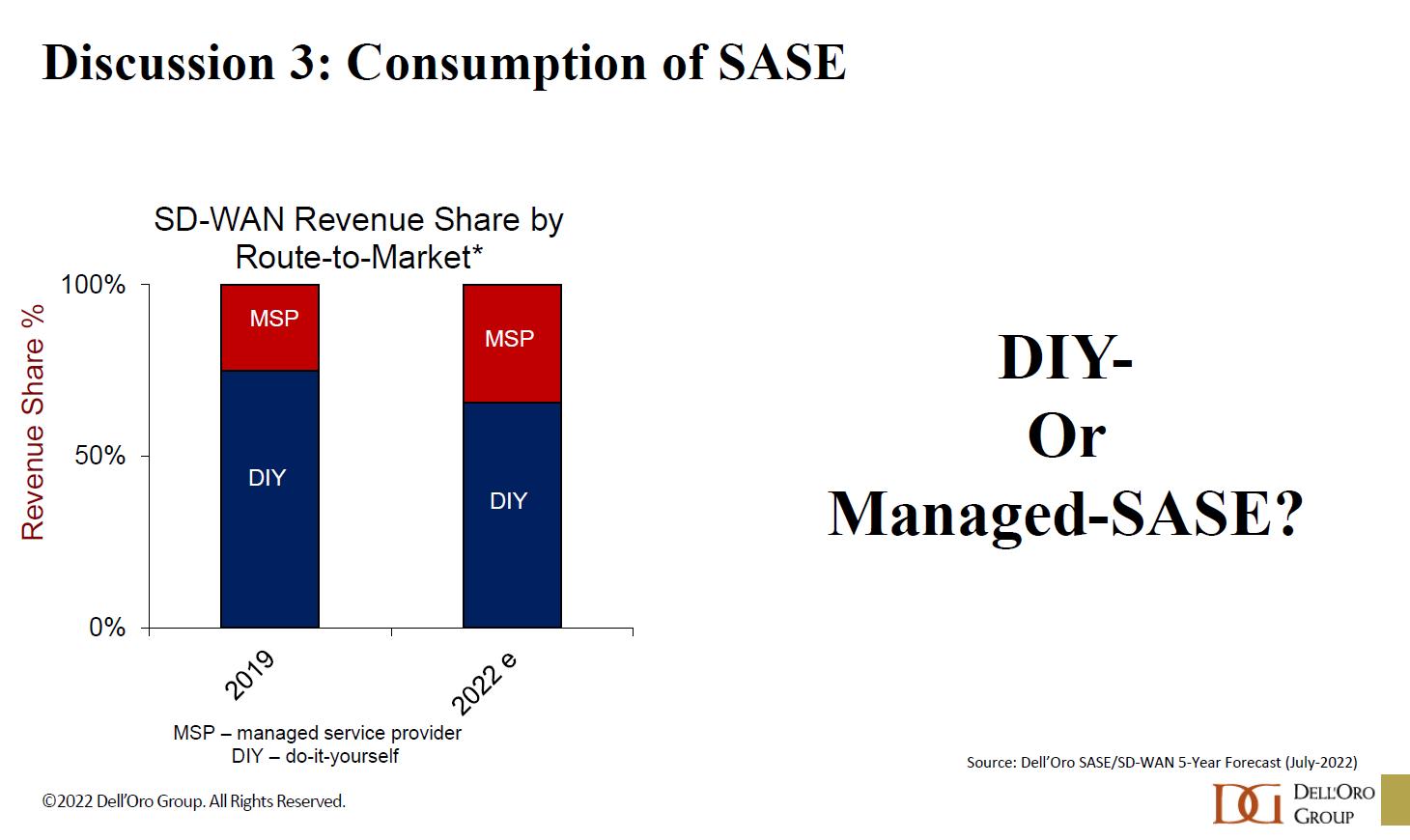
Cohn sees a couple of factors that might hinder adoption of managed SASE services: “One of them is that the network and security organizations within many enterprises is traditionally two distinct organizations,” he observes. “And if you’re going to create a converged offering, you have to figure out who you’re going to sell it to. That’s going to change over time, but it won’t happen overnight. The second factor is that if we look at the long-term outsourcing trend, there is a propensity to look at cloud services.”
Connors of VMware knows of scenarios where network engineers prefer one vendor and security engineers prefer another: “That just underscores another shift that is happening, and has to happen, which is that networking and security are converging,” he points out. “That’s not just about the products we offer, but the people building these solutions on the ground. I think there will be a lot of areas where managed services can help as SASE emerges.”
Thakore of Netskope references a recent survey the company carried out among 3,500 CIOs indicating that two thirds think that SASE will change how they structure their teams in future. “If you have separate groups for security and networking, who has budget control?” he queries. “CIOs are in the process of figuring out how they will all structure this. Will they do it themselves. Are we talking independent decisions or ones made together?”
Last word to Connors of VMware: “As customers are converging networking and security one thing we can do is advise on what the landscape looks like and how to unite two different things that have been siloed for so long, whether it’s one vendor or multi-vendor,” he concludes. “We need to talk to them about ROI, achieving simplicity and meeting use cases. That’s where the expertise of managed service can really come in and help.”





