Feature Stories

Inaugural Point Zero Forum Wraps Up
The Swiss Secretariat for International Finance (SIF) and Elevandi have concluded the three-day, in-person-only Point…

Bitdefender’s Big Hires Across ANZ
Bitdefender has announced two key additions to its Australian Business Solutions Group team. Kevin Dyson…

BT’s Connected Cloud Edge
BT has announced the launch of a next-generation cloud connectivity solution designed to accelerate customers’…

French Korean Conference and High-Performance Computing
On June 23rd 2022 a high-level event jointly organised by the French Embassy and Atos…

Surge in 5G Subscriptions Across APAC
The top 20 telecom operators in the Asia-Pacific (APAC) region reported a year-on-year (YoY) cumulative…

New Relic Launches Partner Stack
New Relic has announced the availability of New Relic Partner Stack. While the observability market…
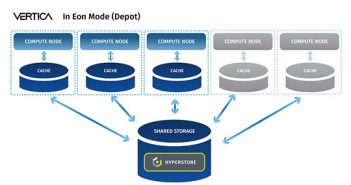
Cloudian Partners with Vertica
Cloudian has announced a partnership with Vertica for managing their artificial intelligence/machine learning (AI/ML) and…

Advent One Adds Another Layer 8 to its Network
Advent One has announced it has acquired Layer 8 Networks. Layer 8 Networks, founded by…

Inaugural Fortinet Ultimate Fabric Challenge Global Championship
Ben Le Huray, solution architect team leader, Ingram Micro Australia has won the inaugural global…

Ingram Micro Powers Up Channel for Cybersecurity Delivery
Ingram Micro has announced the launch of its Cybersecurity Practice Builder, which is backed by…

Oracle Expands Distributed Cloud Services
Oracle Cloud Infrastructure (OCI) has announced the introduction of a lower entry point for OCI…

DigiCert Acquires DNS Made Easy
DigiCert has announced it has acquired DNS Made Easy, as well as affiliated brands, including…

Varonis Appoints Former Proofpoint Manager
Varonis Systems has announced it has appointed Zane Lockley to the newly created position of…

Lenovo Opens First European In-House Manufacturing
Lenovo has officially opened the doors to its first in-house manufacturing facility in Europe. Based…

